What is Metasploit?
Metasploit is a powerful open-source framework used for penetration testing, security assessments, and vulnerability exploitation. It provides a suite of tools that help cybersecurity professionals identify, exploit, and remediate security flaws in networks, applications, and systems. Metasploit includes modules for scanning vulnerabilities, executing payloads, and simulating real-world cyberattacks, making it an essential resource for ethical hacking and defensive security strategies. With its extensive database of exploits and adaptable scripting capabilities, Metasploit allows users to test system resilience and strengthen defenses against potential threats.

First Things First
To get started, you’ll need a homelab. You can check out my article on setting up a homelab here for guidance. Next, download a Kali Linux VHD from kali.org and set it up in VirtualBox. Once that’s ready, follow my Metasploitable2 setup guide here to complete your environment, ensuring you have everything needed for this project.

Lets Get Started
Launch VirtualBox and start your pfSense machine if you’re incorporating a firewall and IDS into your setup. Otherwise, simply start your Kali Linux machine along with the Metasploitable2 VM. Once both virtual machines are up and running, log into your Kali machine and open the terminal to begin your testing and security analysis.
Find the IP of Metasploitable
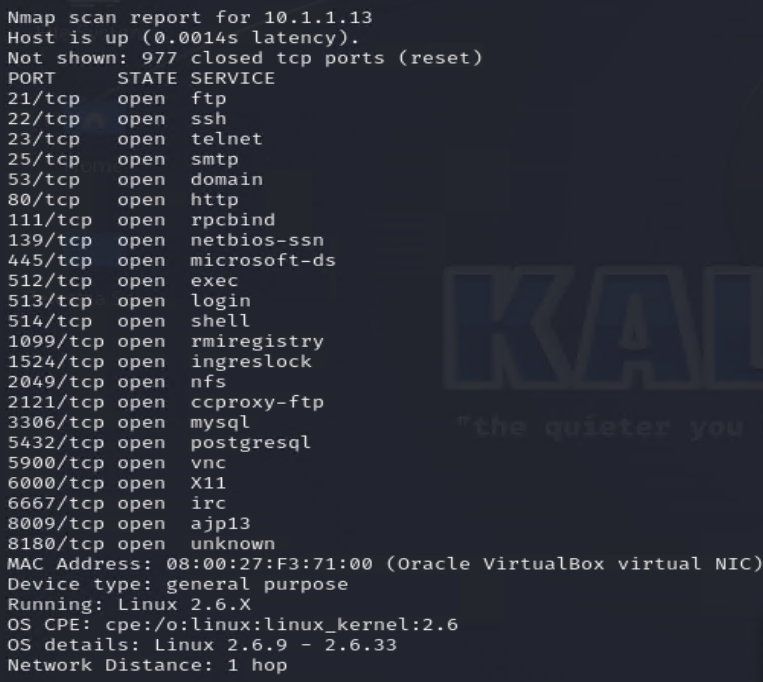
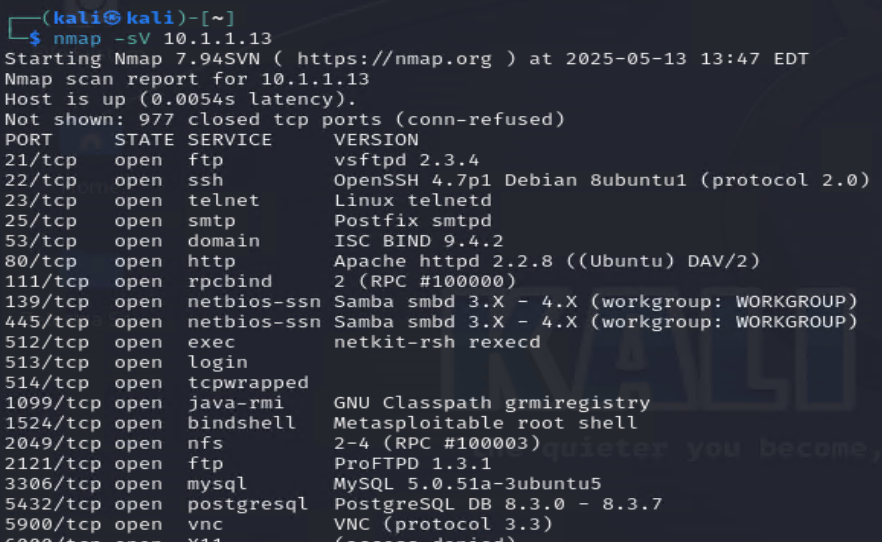
To identify the IP address of your Metasploitable2 VM, you’ll need to perform a network scan using Nmap. If you already know the IP, you can skip this step; otherwise, running a subnet scan will reveal active devices. In a /24 subnet, executing nmap -O 10.1.1.0/24 will list available hosts, their operating systems, and any open ports. In this example, a Linux-based machine with multiple open ports was found at 10.1.1.13, indicating the Metasploitable2 instance. Once you have the IP address, you can proceed with testing and exploitation using Metasploit, ensuring you correctly target the virtual machine for security assessments. Accurately identifying the machine’s IP is a crucial step in penetration testing, as it allows for effective interaction with vulnerable services and a deeper exploration of potential weaknesses.
Identify service versions for vulnerabilities.
You can use Nmap to identify service versions by running nmap -sV followed by the IP address of your Metasploitable2 VM. This command will scan active services and display version details, helping you determine which ones may be vulnerable. In this case, the scan reveals an FTP server running a known vulnerable version. The National Institute of Standards and Technology (NIST) has assigned this service a Common Vulnerability Score (CVSS) of 9.8, indicating a critical security risk due to an embedded backdoor that can open a shell. Understanding service versions is a crucial step in vulnerability assessment, allowing testers to identify weaknesses and simulate real-world attack scenarios.
Lets Exploit the Vulnerability
Step 1
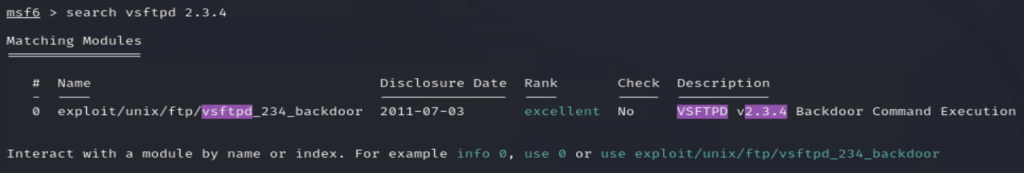
Now that we have identified the vulnerable service and its version, we can leverage Metasploit to exploit the security flaw efficiently. Metasploit simplifies the process, allowing us to search for pre-built exploits tailored to the specific vulnerability. To begin, launch Metasploit by opening a terminal and running msfconsole. Once it initializes, we can use the search function to locate an appropriate exploit by entering search vsftpd 2.3.4, which corresponds to the service version identified in our Nmap scan. Metasploit will then display relevant modules designed to target this vulnerability, enabling us to proceed with selecting and executing the exploit. From here, we can begin interacting with the compromised system, gaining valuable insights into penetration testing techniques and security assessments. Understanding how to effectively exploit these vulnerabilities is an essential skill for cybersecurity professionals aiming to enhance their ability to assess and mitigate real-world threats. Let me know if you’d like any refinements!
Step 2
After searching for the exploit in Metasploit, you’ll notice that there is only one available option, labeled as option 0. To use this exploit, simply type use 0 in the terminal. Next, set the RHOST parameter to the IP address of your Metasploitable2 VM, ensuring that Metasploit correctly targets the vulnerable machine. Once this is configured, you’re ready to launch the exploit. Just type exploit, and if successful, a shell session will open, granting direct access to the Metasploitable2 system. At this point, you’re officially inside, allowing you to interact with the compromised machine and begin further security assessments. This moment highlights the effectiveness of penetration testing tools in demonstrating vulnerabilities and reinforcing the importance of securing exposed services.
Your In!
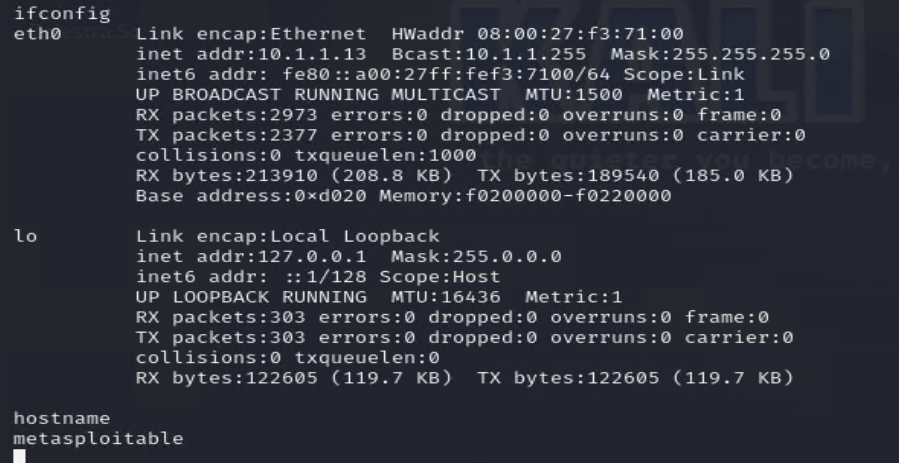
To confirm that you have successfully gained access, run the ifconfig command to check the IP address of the compromised system. If the IP matches the address identified in your Nmap scan, then you’ve effectively connected to the Metasploitable2 machine. Additionally, you can verify the system’s identity by executing the hostname command—if it returns “Metasploitable”, you’ve successfully exploited the vulnerability. This process highlights how simple it can be to compromise outdated or vulnerable services, reinforcing the importance of keeping systems updated and properly secured to prevent unauthorized access. Regular patching and security best practices are essential for mitigating potential threats and ensuring system integrity.